Red Team
Unlike traditional penetration testing, Red Team testing is a more comprehensive and in-depth security assessment method designed to evaluate an organization’s overall security mechanisms. In this service, employees, applications, networks, and physical security measures are tested by experienced ethical hackers (Red Team) using various techniques and perspectives.
Red Team tests mimic real-world attack methods to simulate scenarios that target critical data and assets within the organization. The goal is to identify security gaps, assess the effectiveness of security measures, and provide recommendations for addressing potential vulnerabilities.
Our Red Team service allows for a more proactive approach to cybersecurity, providing realistic tests of your organization’s security defenses. This service offers a multifaceted evaluation process that encompasses not only digital infrastructure but also the human element and physical security.
At Invento, our Red Team services aim to maximize your organization’s resilience against real-world attacks, enhancing cybersecurity defense to the highest level.
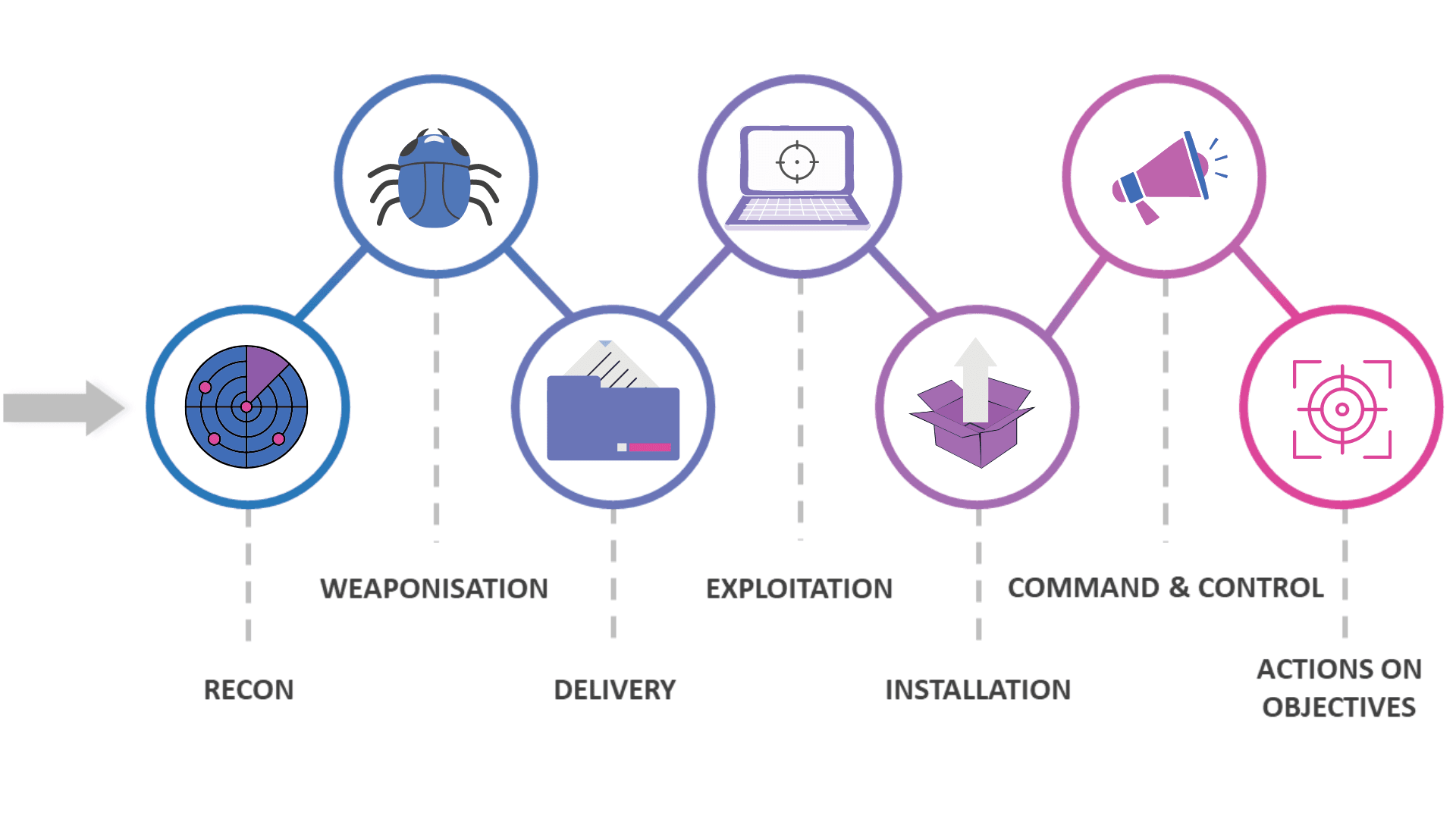
Stages of Red Team Testing
Red Team testing is an extensive security evaluation process designed to identify security vulnerabilities by simulating real-world attack scenarios. The testing process consists of several critical stages, each aimed at a thorough analysis of the organization’s security posture.
Discovery (OSINT)
The reconnaissance stage involves gathering as much information as possible about the target organization’s external and internal dependencies, connections, applications, employees, and publicly available resources. This phase is divided into passive and active scanning. The more comprehensive and detailed the reconnaissance, the more successful the Red Team process will be.
During this phase, techniques like dorking are used to collect detailed information about the organization’s infrastructure, domain structure, and third-party applications and technologies in use. This information forms the basis for attack scenarios in the later stages.Threat Modeling
Based on the information gathered during reconnaissance, potential attack scenarios that could impact the target organization are developed. In this stage, possible attack techniques and methods are identified, thinking like a real attacker. The target could be an employee, a phishing (social engineering) attack, a physical device, or any public-facing application. The objective is to identify the organization’s weakest points and develop effective attack scenarios against these vulnerabilities.
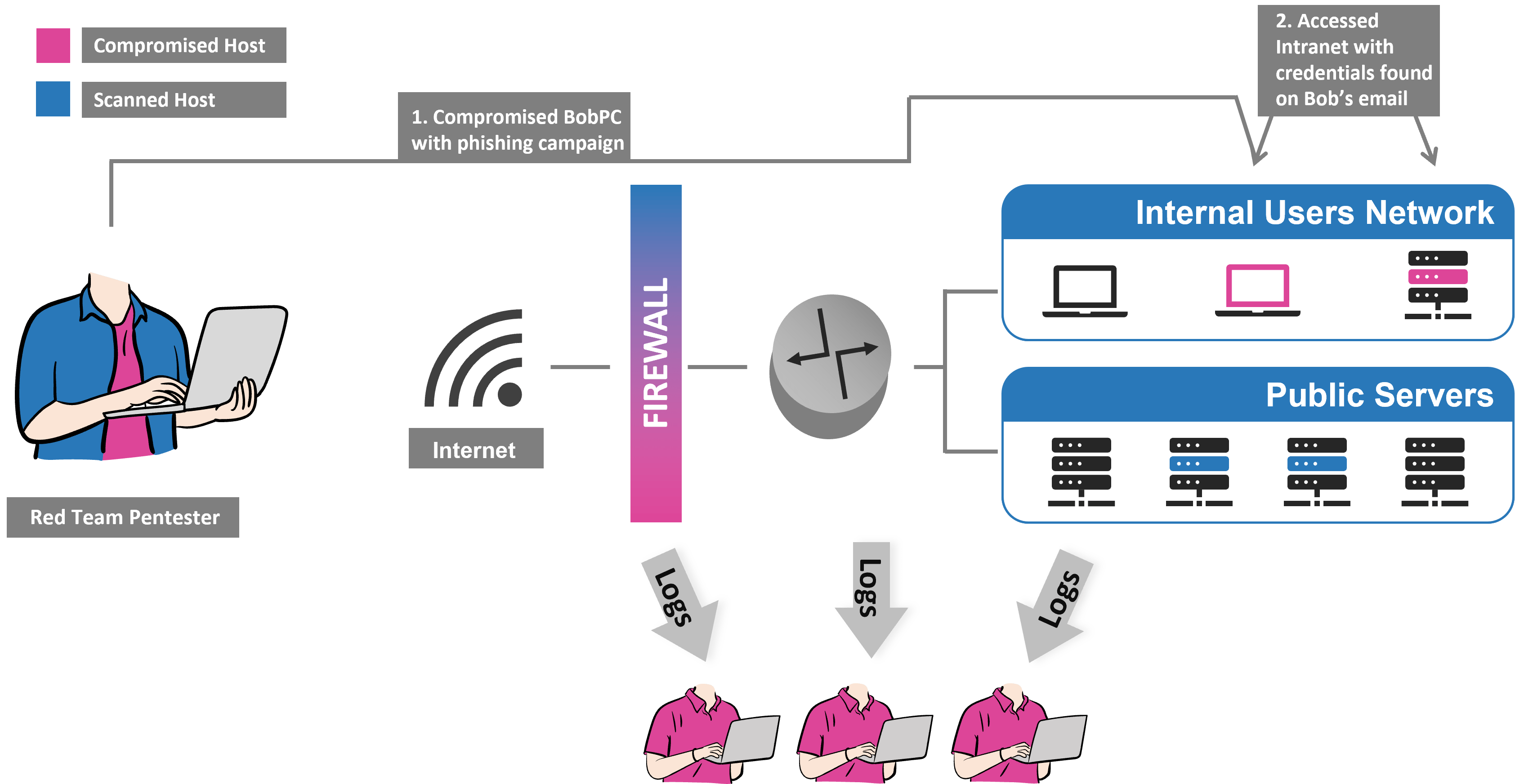
Initial Access
In this stage, various methods are used to detect security vulnerabilities within the target organization. This phase focuses on exploiting known vulnerabilities, developing phishing scenarios to plant malware, conducting physical attacks, network attacks, or web application-based attacks. Vulnerability analysis is a key step in uncovering the organization’s security weaknesses.
Exploitation
During the attack simulation stage, realistic attacks are carried out based on the identified vulnerabilities. Targeted attack scenarios, such as gaining internal network access or reaching sensitive data, are executed in this phase. Depending on the success achieved, advanced attack techniques like privilege escalation, lateral movement, pivoting, and identity spoofing may also be employed. This phase is critical for testing the robustness of the organization’s security mechanisms.
Reporting and Evaluation
The final and most critical stage of the Red Team testing process is reporting. This stage involves providing a comprehensive report that details all findings, vulnerabilities, and executed attack scenarios. The report documents each step from point A to point B and the outcomes of each action.
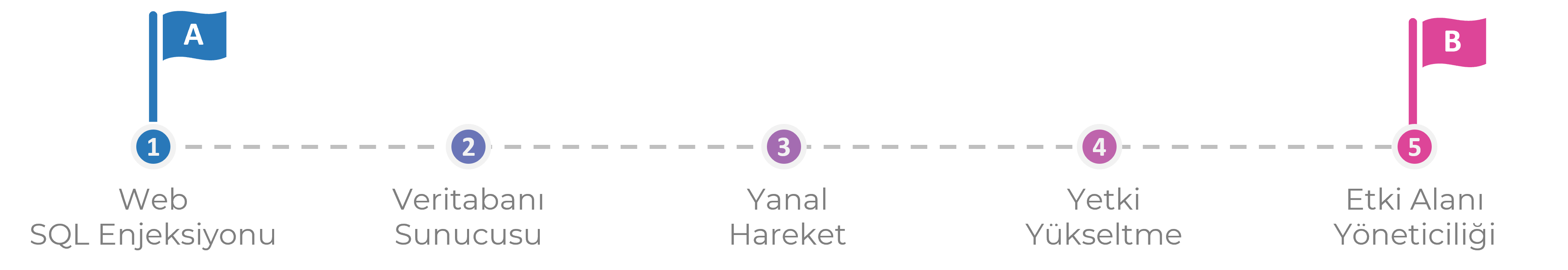
The report explains the critical severity levels and potential impacts of the identified vulnerabilities. It also includes solution recommendations, supporting reference links, and improvement steps.
During the reporting phase, all gathered data is carefully cleaned, and any changes made to the organization’s environment are restored to their original state. This process provides clients with the necessary information to make informed decisions and prepares them to handle future attacks more effectively.