Zero Trust Segmentation in Banking and Financial Services
Banks and other financial institutions are turning to Zero Trust Segmentation to guard against ransomware and similar cyberattacks that can trigger financial losses and reputational damage.
Modern Bank Robbers Are Zeroing in on Financial Services
Banks, investment houses, retail brokerages, lenders, fintech startups and other financial services institutions are the proverbial “big game” for cybercriminals. The reason is simple: That’s where the money is.
Financial services was the top industry targeted by cybercriminals for five consecutive years of 2016-2020, according to an IBM report. In 2021, financial services accounted for 22.4% of attacks, in second place just behind manufacturing – but still very much a prime target for ransomware and other cyberstrikes.
Of attack types, ransomware was far and away the most prevalent in financial services, accounting for 36 percent of attacks across all industries, IBM reported.
Risk of a cyberattack is heightened as banks and other institutions undergo digital transformation, introduce new cloud systems, and expand partnerships with third-party products and service providers. Brisk M&A activity, continued use of legacy IT and cybersecurity systems, and a shift to remote work can also erode an institution’s security posture.
Those technological and business changes broaden the attack surface and pose new challenges to visibility. Detecting and identifying a breach is becoming more difficult across complex and interconnected networks. If a breach does occur, a bank can suffer sizable financial losses and negative publicity that undermine confidence among commercial and retail customers, business partners, counterparties, investors and regulators.
Guarding against ransomware and other kinds of cyberattacks has become more than just a cybersecurity problem – it’s now a business resilience challenge at the highest levels.
In this guide, we explore the unique cybersecurity challenges facing banks and other financial services providers. We examine how Zero Trust Segmentation provides an invaluable defense that protects both the financial institution and its customers across a rapidly changing landscape.
Illumio Zero Trust Segmentation in Banking and Financial Services
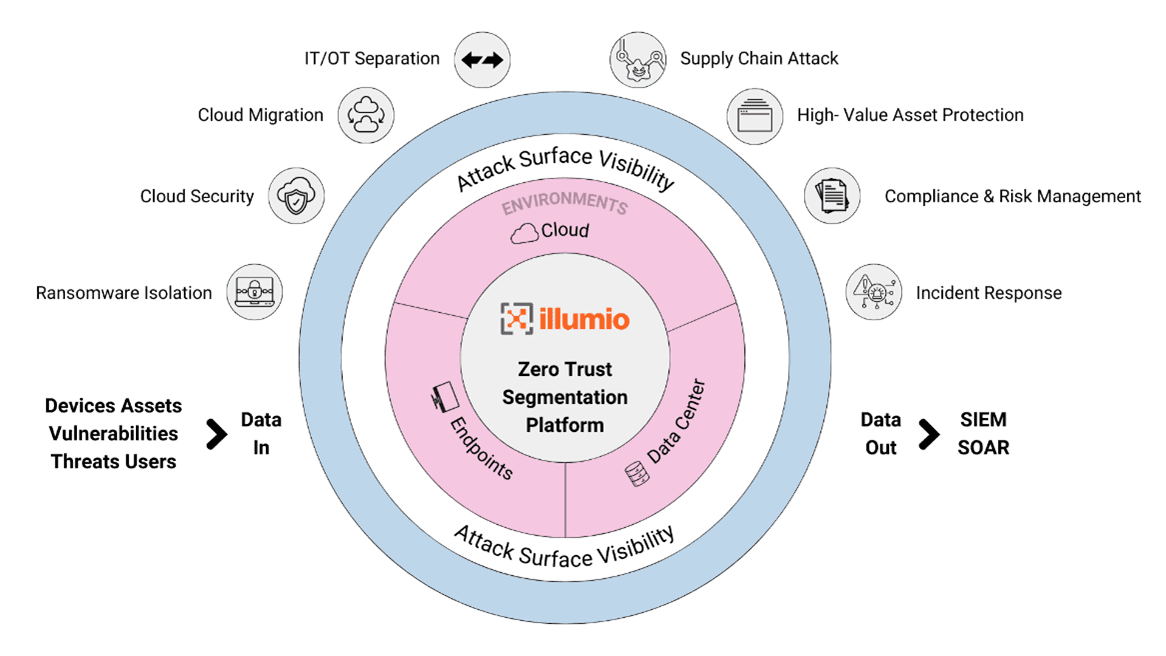
Illumio’s Zero Trust Segmentation technology enhances traditional perimeter and firewall defenses to embed security at a far more granular level into the interior of networks and data centers. Instead of a single firewall protecting hundreds of applications and devices, security is applied at each asset individually.
Financial services CISOs use Illumio to help achieve three top objectives of protecting customer data, achieving regulatory compliance, and enabling digital transformation:
- Protect customer data by understanding access to systems, implementing security policies to limit systems access, and reporting and analyzing all traffic that doesn’t match rules.
- Achieve regulatory compliance by scoping vulnerabilities across the full environment, mapping application dependencies, applying granular segmentation policies, and monitoring connectivity for vulnerability and compliance violations.
- Enable digital transformation with visibility into relationships between data center and cloud components, by securing both on-premises and cloud applications consistently, and by integrating with DevOps processes to automate security at scale.
Zero Trust Benefits in Banking
The Bank Policy Institute cites security and business benefits in recommending that banks adopt Zero Trust security:
- Reduced attack surface
- Improved application and data protection
- Enhanced visibility across assets
- Reduced risk of malware
- Faster breach detection
- Continuous security compliance
- Streamlined mergers and acquisitions
Segmentation Security, Ransomware Containment and Visibility
Named a Leader in The Forrester New Wave™: Microsegmentation, Q1 2022, Illumio’s core capabilities equip banks and other financial institutions to:
- Secure critical assets and services, even inthe event of a breach.
- Stop the spread of ransomware acrossnetworks, data center servers andapplications.
- Realize comprehensive visibility acrossapplications, devices and networks.
1. Secure Critical Assets and Services
Illumio Zero Trust Segmentation ensures thataccess to any asset or application is secure andauthenticated. It eliminates paths that allowlateral movement and enforces and maintainspolicy within large, rapidly changingenvironments. With Illumio, you can:
- Easily segment assets, environments, usersand groups. Build Zero Trust access rules
through data-driven policy design, automatic policy creation, and scalable enforcement using your existing network and device infrastructure. - Enforce policies dynamically to consistentlysecure evolving applications, devices andnetworks. Write simple rules to govern accessand communications across internal andpartner systems. Policies will automaticallyupdate as systems change.
- Operate at the host level. Manage existinghost-based firewalls that scale easily. Managedfrom a single console, all without movingcables or changing your virtual infrastructure.
Illumio stops ransomware in ways that legacy security tools simply cannot. With Illumio, you will reduce your attack surface, limit the blast radius of a successful breach, and protect your most sensitive data, applications and assets.
2. Contain Ransomware
Illumio immediately shrinks your attack surface by automating workflows — like policy discovery, authoring, distribution and enforcement — that block communications on any high-risk port in your network. With Illumio, you can:
- Pinpoint your critical sources of ransomware risk. See all of your commonly exploited pathways, orphaned legacy connections, and data flows that are out of compliance with your existing security policies.
- Proactively close and monitor high-risk pathways. Close commonly exploited ports in your environment while monitoring those ports that must remain open.
- Create a reactive containment switch to stop in-progress incidents. Develop a one-click solution that can precisely block communications down to the workload level, isolating and protecting unaffected systems during an incident.
3. Visualize Device and System Communication
Illumio provides actionable insights by mappingall communications between assets, includingapplications, clouds, containers, data centers andendpoint devices. And it does this withouttouching or changing your network. WithIllumio, you can:
- Build real-time network visibility.Automatically map the internalcommunications and outbound Internetconnections for each of your applications,systems and workloads.
- Lower operational risk by identifyingunnecessary connections. Build a clearpicture of your vulnerable systems,noncompliant data flows, and excessivecommunications. You’ll gain a betterunderstanding of what’s open and why.
- Share a unified view of yourcommunications for your teams and yourSIEM/SOAR tools. Create tight collaboration,offering customized views for Network Ops,Security Ops, DevOps and DevSecOps. Feedreal-time data to your SIEMor SOAR.
Zero Trust benefits in banking
The Bank Policy Institute cites security and business benefits in recommending that banks adopt Zero Trust security:
- Reduced attack surface
- Improved application and data protection
- Enhanced visibility across assets
- Reduced risk of malware
- Faster breach detection
- Continuous security compliance
- Streamlined mergers and acquisitions
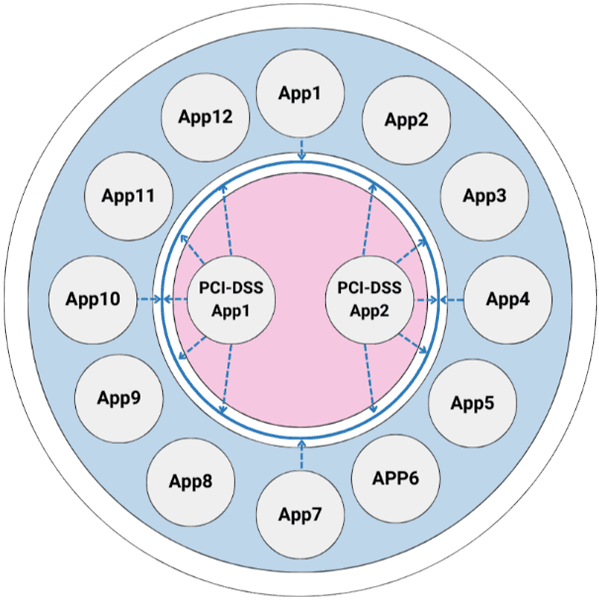
Sample use case with PCI-DSS
PCI-DSS requirements dictate that controls be in place around a cardholder data environment (CDE) to ensure that PCI data is contained within a boundary.
Illumio lets you easily define an enforcement boundary to segment PCI-DSS apps and non-PCI-DSS apps. That ensures that all traffic across the cardholder data environment is on an explicit allowlist, quickly and effectively addressing the PCI-DSS compliance requirement.
Illumio’s visibility allows you to clearly see the full scope of a CDE. As a result, you avoid needlessly expanding segmentation across out-of-scope systems at significant time and cost, or making segmentation too narrow and jeopardizing compliance.
Network-Based Segmentation vs. Host-Based Segmentation
There are various ways of implementing segmentation. Some financial institutions try configuring their network switches and routers and perimeter firewalls to implement network segmentation controls, but that typically leads to two problems.
First, it’s difficult to translate high-level policies into detailed networking rules on switches, routers and firewalls. For example, it’s nearly impossible to create a practical networking rule based on a high-level policy that a web application should have network access only to the services it needs to perform its intended functions.
Inevitably, rules programmed into network gear end up being too strict or too lax. As a result, either application functionality or security resilience suffers.
The second problem is a lack of precision. With thousands or tens of thousands of endpoints on a network, it’s difficult to enforce endpoint-specific controls from network gear and perimeter firewalls.
A better solution is to implement Zero Trust Segmentation on individual endpoints themselves. This approach takes advantage of the host-based firewalls built into endpoints such as laptops and servers. A host-based approach offers these advantages:
- Direct, simplified control
It’s easier to enforce security rules for endpoints like laptops on the endpoints themselves rather than on network devices like routers and firewalls. Network firewall rules are overly complex as it is withouttrying to implement access controls that, for instance, differentiate a manager from a subordinate in a particular department.
- Segmentation that works everywhere
Enforcing segmentation rules on endpointsthemselves is much more practical now thatso many employee endpoints are used inremote locations like home offices. If anemployee isn’t on an internal network,internal network devices can’t enforcesegmentation rules. Host-basedsegmentation enforces segmentationpolicies wherever an endpoint happensto be.
- Pinpoint accuracy for rapidlyisolating threats
Security teams can use an endpoint’s host-based firewall to isolate the endpoint if theysuspect it has been compromised. Becausethe firewall is on the endpoint itself, itisolates only the affected network, not thewhole LAN or VLAN to which the endpoint isconnected. Security teams don’t have to riskmisconfiguring firewalls as they rush toisolate an endpoint or, once an incident isresolved, to restore its connectivity.